Customer-Managed Encryption Keys in Rockset
October 31, 2023
Securing customer data is of the utmost importance for companies large and small. Regulation and hefty legal ramifications are front and center for security teams tasked with ensuring sensitive data stays out of the hands of unauthorized external and internal personnel.
Encryption plays a key role in making the above possible. While Rockset applies its own encryption keys to customers’ data, some security teams want to own their own destiny when it comes to managing the rotation schedule as well as having an emergency ‘break the glass’ mechanism in case of a breach. To enable this, Rockset collection data can now be encrypted at rest with Customer-Managed Encryption Keys, also often referred to as bring your own key (BYOK). Customers remain in complete control of the key, while granting the Rockset AWS account permission to encrypt and decrypt data using that key.
Configuring Customer-Managed Encryption Keys
To ensure compatibility with this feature, customers must follow the instructions from the Rockset documentation to create an AWS Key Management Service (KMS) key. Once the organization is created and linked to the customer provided KMS key ARN, all collections created on that organization are encrypted at rest using that key. The encryption key ARN cannot be changed after the organization is created, but customers can optionally enable automatic key rotation on the provided key.
Behavior When the Key is Unavailable
Once created, Rockset organizations using a Customer-Managed Encryption Key behave in exactly the same way as any other Rockset organization - the only difference is the encryption key used to protect the collection data. However, customers are able to disable or change the policy configuration of the provided KMS key. Disabling access to the key will prevent Rockset from being able to encrypt new data or decrypt existing collection data, resulting in query and ingestion failures within minutes.
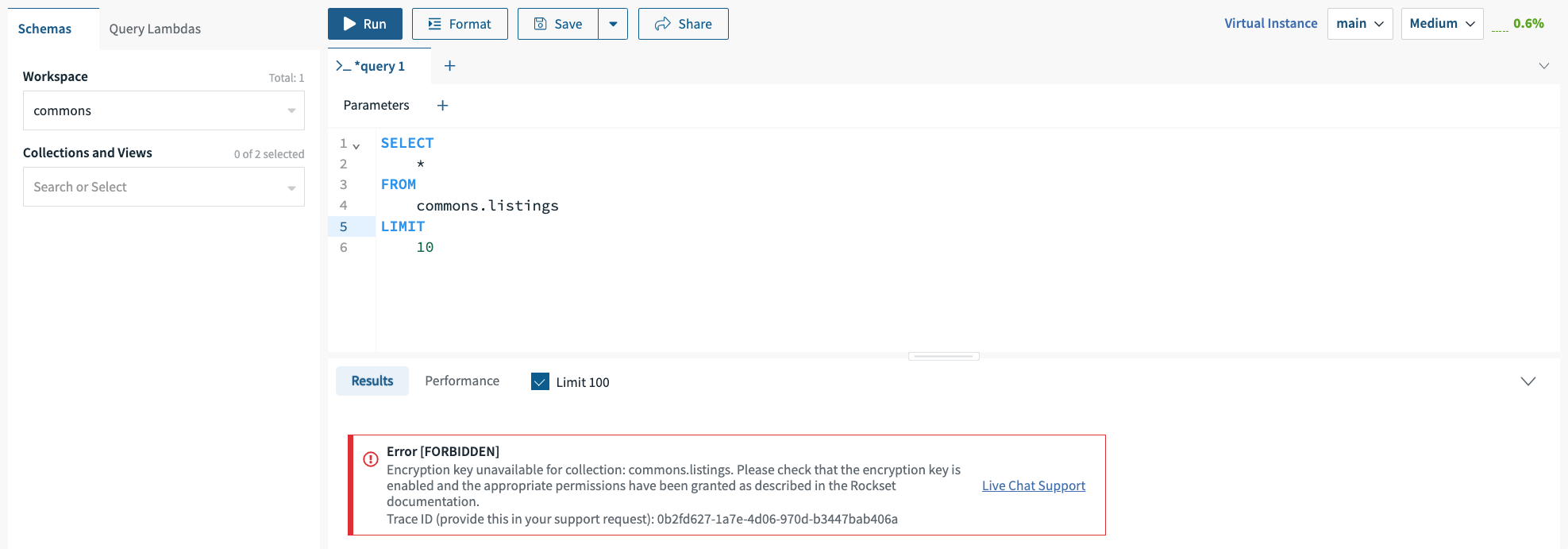
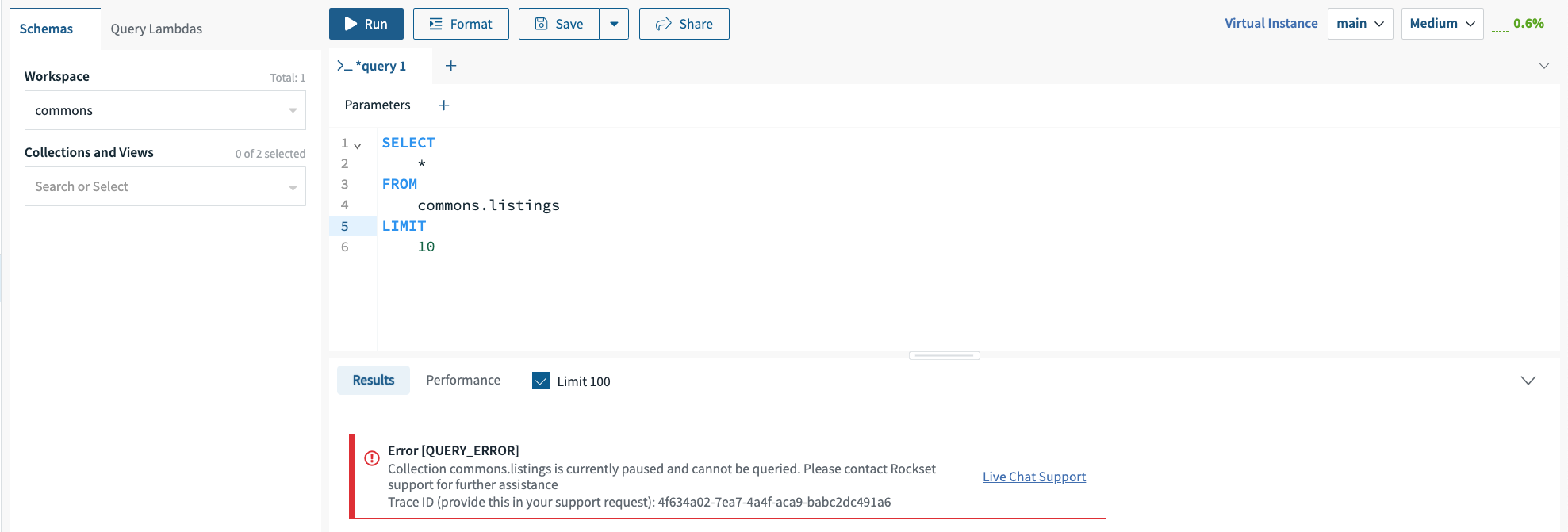
If Rockset regains access to the key promptly, queries and ingestion become available within minutes. However, if the KMS key remains unavailable for several hours, all collections within the organization are paused, and data in transit and caches are purged. This prevents Rockset from accessing any customer collection data. Collections that are paused due to key unavailability for several hours become unrecoverable.
For more information on how you can use customer-managed encryption keys in your Rockset organization, please check our Customer-Managed Encryption Keys guide.